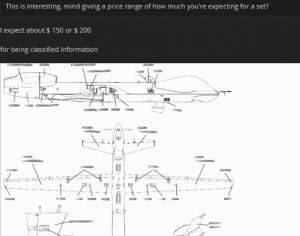
Security firm Recorded Future has discovered that last month, an unidentified hacker stole sensitive military documents and tries to sell it online via hacking forums. The selling price for such docs run as low as $150 – $200. The data was allegedly hacked from the computer of an Air Force officer. It said to contain sensitive information about the MQ-9A Reaper drone that is used for overseas strikes and surveillance missions. This could give an enemy clues into its technical capabilities and potential weaknesses.
However, the firm confirmed that there was no evidence the mystery hacker was tied to a foreign country. It posed as a potential buyer and based on their exchanged messages with the mystery hacker, the firm suspects that he/she could be from South America because the communication is sometimes in Spanish and of broken English.
Also for sale are various training manuals such as a crewman training and survival manual, deployment tactics manual for improvised explosive devices (IED), and a tank operation manual.
Recorded Future already informed Homeland Security about the alleged hack and so the hacker was blocked from selling the said sensitive documents while the issue is currently being investigated.